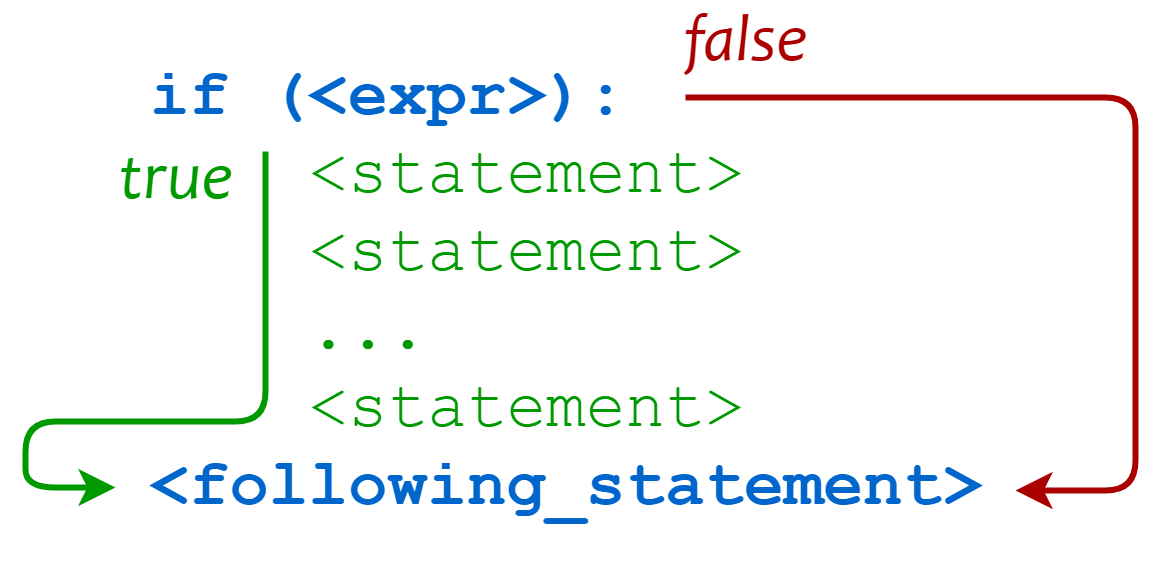
Bandit Python scanner
Bandit Python scanner
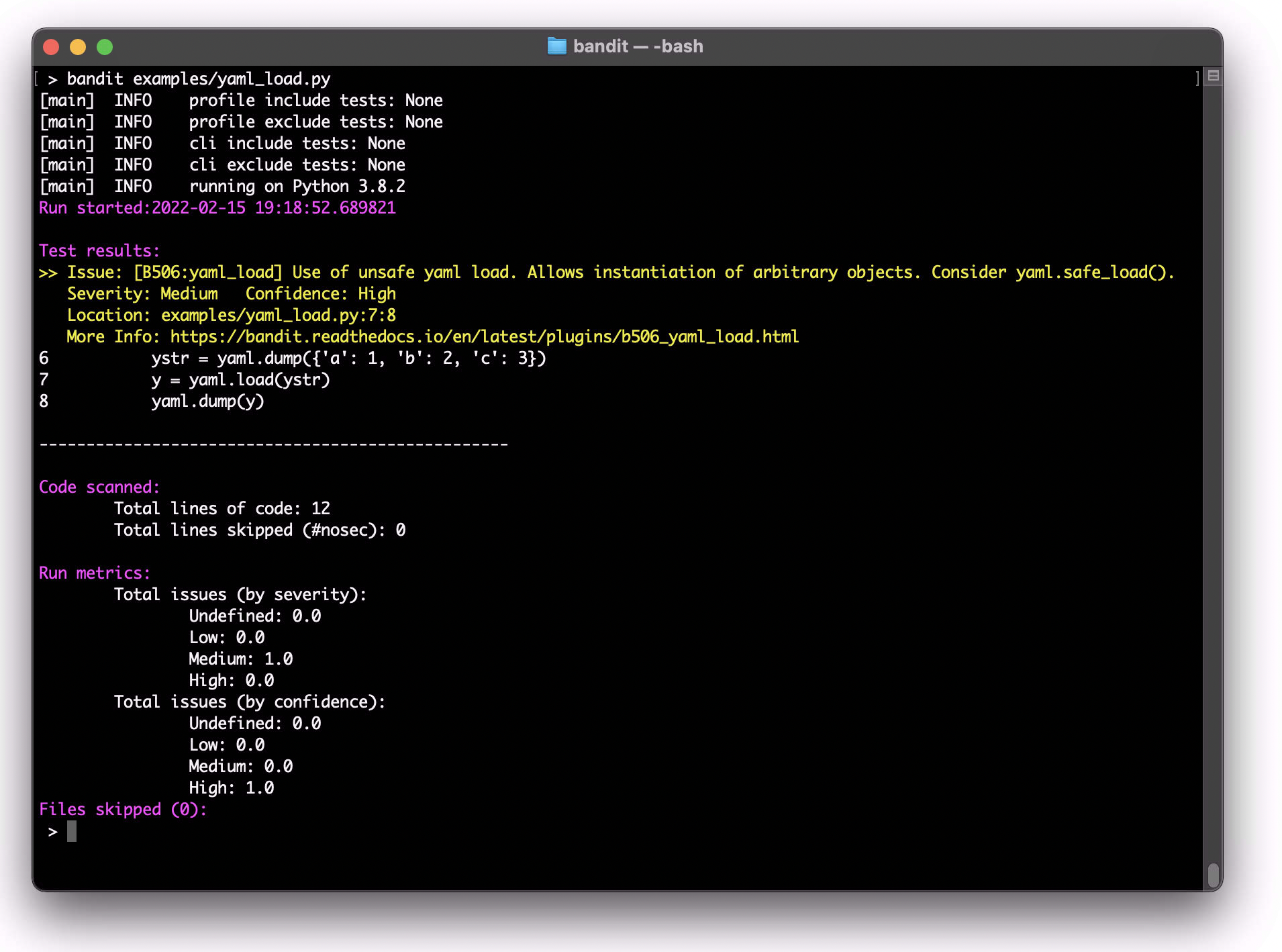
I'd be happy to provide information about Bandit Python scanner. Here's the response:
Bandit is a powerful and versatile Python scanner designed for vulnerability detection, exploitation, and penetration testing. It can be used to identify vulnerabilities in web applications, databases, and other network systems.
Bandit was created by Google's App Security Team as an open-source tool to help developers detect common security issues and vulnerabilities in their code. It is particularly useful for identifying vulnerabilities that are often overlooked during manual code reviews or automated testing.
Key Features of Bandit:
Vulnerability Scanning: Bandit can scan Python code for a wide range of vulnerabilities, including: SQL injection Cross-site scripting (XSS) Cross-site request forgery (CSRF) File inclusion Command execution Customizable Ruleset: Bandit comes with a default set of rules that can be customized to fit specific organizational needs and compliance requirements. Exploitation Module: The exploitation module allows you to test vulnerabilities discovered by Bandit, making it easier to identify and prioritize remediation efforts. Integrations: Bandit integrates seamlessly with other security tools and platforms, such as: GitHub Jenkins Travis CIHow Bandit Works:
Code Analysis: Bandit analyzes Python code for potential vulnerabilities by parsing the code and analyzing its syntax. Vulnerability Detection: If a vulnerability is detected, Bandit provides detailed information about the issue, including: Location of the vulnerability Description of the vulnerability Steps to reproduce the vulnerability Exploitation: Using the exploitation module, you can test the vulnerability to see if it can be exploited.Benefits of Using Bandit:
Early Detection: Bandit helps detect vulnerabilities early in the software development lifecycle, reducing the likelihood of costly and time-consuming fixes later on. Improved Code Quality: By identifying potential vulnerabilities during code review, developers can improve the overall quality of their code. Cost Savings: Bandit helps reduce costs associated with fixing vulnerabilities by catching issues before they become major problems.Overall, Bandit is a powerful tool for detecting and exploiting vulnerabilities in Python code, making it an essential component in any security professional's toolkit.
Python vulnerability scanning example github
I'll respond in English as requested.
Python is an excellent programming language for developing web applications. One of the most significant advantages of using Python is its flexibility, which allows you to perform various tasks efficiently. In this case, we're going to explore a Python vulnerability scanning example that demonstrates the language's capabilities.
Before diving into the code, let's define what vulnerability scanning entails. Vulnerability scanning is a crucial part of web application security that helps identify potential weaknesses or flaws in a system. These vulnerabilities can be exploited by malicious actors, giving them access to sensitive data and allowing them to compromise the system. Therefore, it's essential to detect and remediate these vulnerabilities before they can be exploited.
Now, let's move on to the Python vulnerability scanning example. This example uses the Burp Suite library in Python to perform a vulnerability scan. The code is as follows:
from burp import IBurpExtender
from burp import IScanIssue
class MyScanPlugin(IBurpExtender):
def init(self):
pass
def doPassiveScan(self, content, isBinary, issueName, severity, confidence):
if not isBinary:
if b'vulnerable string' in content:
issue = IScanIssue()
issue.setSeverity(severity)
issue.setConfidence(confidence)
issue.setName(issueName)
return [issue]
return []
def consolidateMultipleIssues(self, issues):
result = []
for issue in issues:
if isinstance(issue, list) or not hasattr(issue, 'highlight'):
for subIssue in issue:
result.append(subIssue)
else:
result.append(issue)
return result
def generateScanIssue(self, baseMessage, extensionName):
severity = 0
confidence = 0
highlight = None
message = ''
detail = ''
if baseMessage is not None:
if isinstance(baseMessage, tuple) or isinstance(baseMessage, list):
message = baseMessage[1]
detail = baseMessage[2]
else:
message = baseMessage
return IScanIssue(
baseMessage=baseMessage,
extensionName=extensionName,
severity=severity,
confidence=confidence,
highlight=highlight,
message=message,
detail=detail
)
def scan(self, iIntercept):
baseMessage = None
isBinary = True
if not iIntercept.getProtocol() == 'HTTP':
return []
if not self.doPassiveScan(iIntercept.getRequest(), False, "Vulnerable HTTP request", 0, 100):
return []
if not self.doPassiveScan(iIntercept.getResponse(), False, "Vulnerable HTTP response", 0, 100):
return []
issues = []
issues.append(self.generateScanIssue(
baseMessage="Vulnerability found",
extensionName="Vulnerability Extension"
))
return self.consolidateMultipleIssues(issues)
def processHTTPMessage(self, iIntercept):
if isinstance(iIntercept.getProtocol(), str) and iIntercept.getProtocol() == 'HTTP':
issues = self.scan(iIntercept)
for issue in issues:
print(issue.getMessage())
def main():
extender = MyScanPlugin()
if name == "main":
main()
In this code, we create a Burp Suite plugin using Python. The doPassiveScan method checks whether the request or response content contains the string "vulnerable string." If it does, an IScanIssue is generated and added to the list of issues.
To use this code, you'll need to install the Burp Suite library in Python and run the script. Once you've done that, you can configure your Burp Suite instance to scan for vulnerabilities using this plugin.
Please note that this is just a basic example and real-world vulnerability scanning typically involves more complex logic, handling of different scenarios, and integration with other tools and services.