Python requests auth Bearer
Python requests auth Bearer
I'd be happy to provide a detailed explanation of how to use the requests library in Python for authentication with a Bearer token.
What is a Bearer Token?
A Bearer token, also known as an access token or JWT (JSON Web Token), is a string that represents a user's identity and permissions. It is used to authenticate API requests and authorize access to protected resources.
How Does it Work in requests?
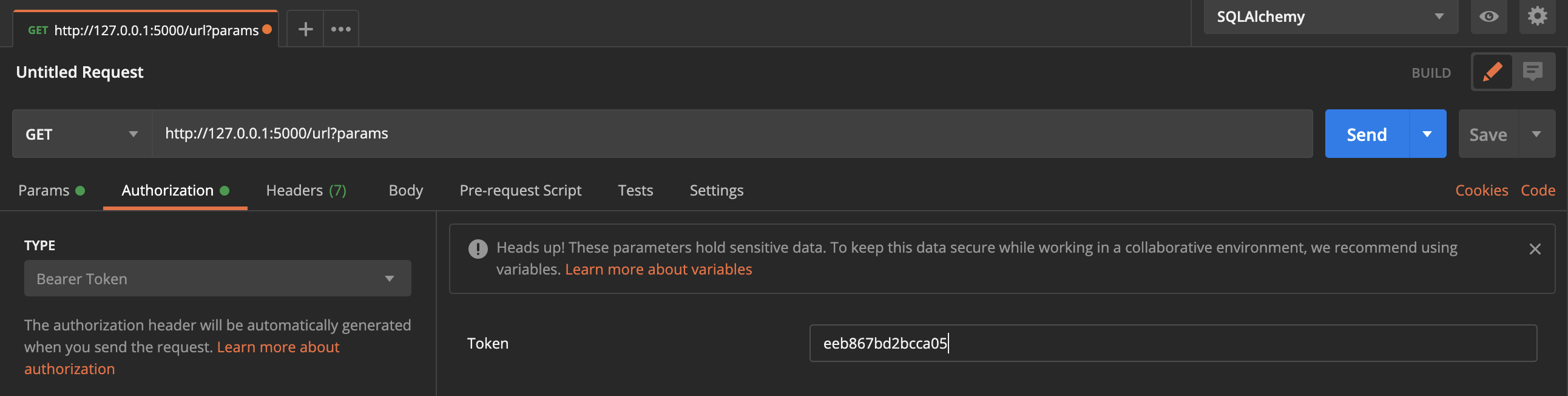
To use a Bearer token with the requests library in Python, you need to pass the token as an authorization header in your request. Here's how to do it:
import requests
Set your API endpoint and credentials
api_endpoint = "https://api.example.com"
username = "your_username"
password = "your_password"
Make a POST request to the login endpoint to obtain the Bearer token
response = requests.post(api_endpoint + "/login", auth=(username, password))
if response.status_code == 200:
Extract the Bearer token from the response JSON
token = response.json()["token"]
Set the Authorization header for subsequent API calls
headers = {"Authorization": f"Bearer {token}"}
Make a GET request to a protected endpoint using the Bearer token
response = requests.get(api_endpoint + "/protected", headers=headers)
if response.status_code == 200:
print("API call successful!")
else:
print("API call failed with status code:", response.status_code)
else:
print("Login failed with status code:", response.status_code)
In this example, we first make a POST request to the login endpoint with our username and password. If the login is successful, we extract the Bearer token from the response JSON. We then set the Authorization header for subsequent API calls using the f"Bearer {token}" format.
Finally, we make a GET request to a protected endpoint that requires authentication using the Bearer token. If the API call is successful, we print a success message; otherwise, we print an error message with the status code.
Best Practices
When working with Bearer tokens in requests, keep the following best practices in mind:
By following these best practices and using the requests library in Python with Bearer token authentication, you can securely interact with APIs and protect your data from unauthorized access.
How to do authentication in Python?
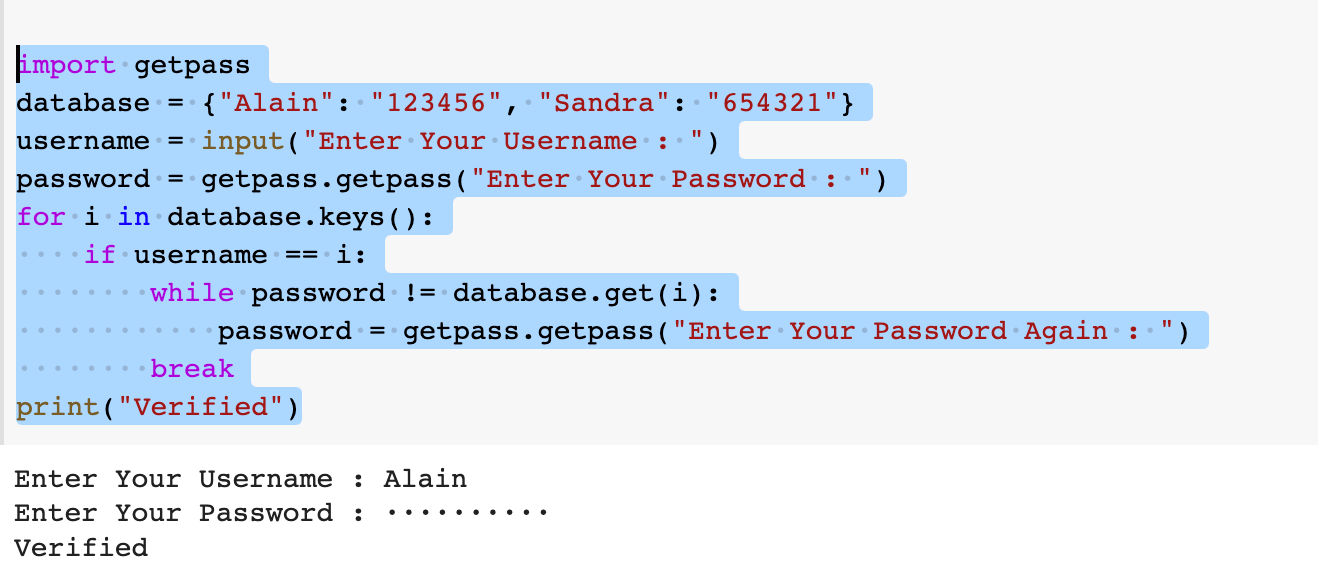
Authentication is the process of verifying the identity and rights of users or systems seeking access to a system, network, or application. In Python, there are several ways to implement authentication, depending on the requirements and constraints of your project. Here's an overview of some popular methods:
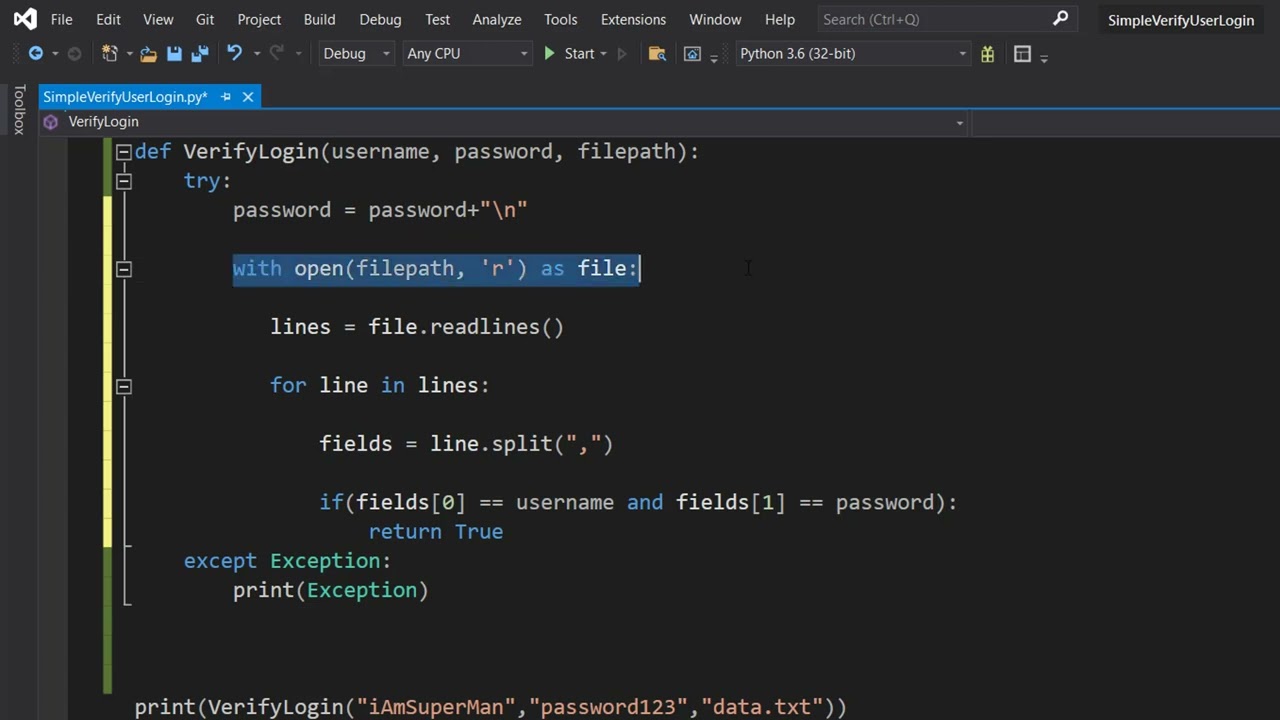
Python provides a built-in http.client module for handling HTTP requests and responses. You can use this to implement Basic Authentication.
import http.client
def authenticate.basic(username, password):
if username == "admin" and password == "password":
return {"user": "admin"}
else:
raise Exception("Invalid credentials")
Example usage
conn = http.client.HTTPConnection("example.com")
headers = {"Authorization": f"Basic {b64encode(f"{username}:{password}".encode()).decode()}"}
conn.request("GET", "/path", None, headers)
response = conn.getresponse()
Python's pyjwt library can be used for encoding and decoding JWT tokens.
from pyjwt import encode
def authenticate.jwe(username):
payload = {"user": username}
return encode(payload, "your-secret-key").decode("utf-8")
Example usage
token = authenticate.jwe("admin")
Python's oauthlib library can be used for implementing OAuth.
from oauthlib.oauth2 import WebApplicationClient
class Authenticator(WebApplicationClient):
def authenticate(self, client_id):
if self.client_secret == "your-secret-client-id":
return {"access_token": "your-access-token"}
else:
raise Exception("Invalid credentials")
Example usage
authenticator = Authenticator(client_id="your-client-id", client_secret="your-secret-client-id")
token = authenticator.authenticate()
Python's datetime and random modules can be used for implementing custom authentication.
import datetime
import random
def authenticate.custom(username):
if username == "admin" and random.randint(0, 1) == 0:
return {"user": "admin"}
else:
raise Exception("Invalid credentials")
Example usage
token = authenticate.custom("admin")
In summary, Python provides a range of options for implementing authentication. The choice depends on the specific requirements and constraints of your project.
Additional Considerations
Security: Always prioritize security when implementing authentication. Use strong encryption, secure passwords, and validate input data to prevent common attacks like SQL injection and cross-site scripting (XSS). Scalability: Authentication can impact scalability. Optimize your code for performance and consider using load balancers or cloud services if you anticipate high traffic. User Experience: Provide a seamless user experience by implementing intuitive, user-friendly authentication mechanisms that minimize frustration and errors. Compliance: Comply with relevant regulations, such as GDPR, HIPAA, and PCI-DSS, when handling sensitive data like passwords and personal information. Testing: Thoroughly test your authentication code to ensure it's working correctly and identify any potential security vulnerabilities.