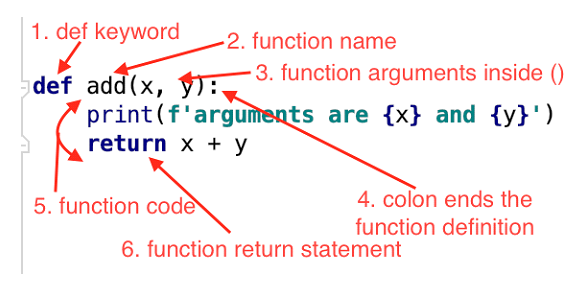
Python hashing calculator
Python hashing calculator
Here's a detailed guide on how to use a Python hashing calculator:
What is Hashing?
Hashing is the process of converting data, such as text or numbers, into a fixed-length string of characters called a hash value or digest. This process is used in various applications like password storage, digital signatures, and data integrity checks.
How Does Hashing Work?
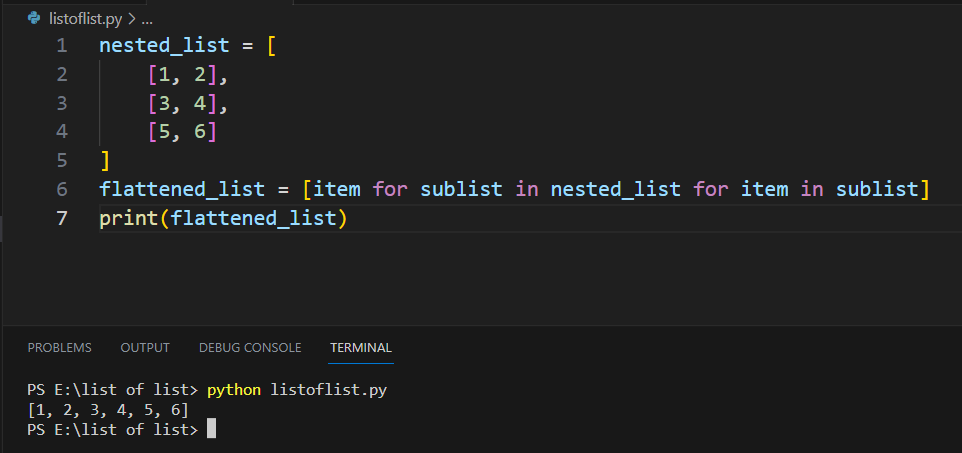
The hashing process involves feeding an input string (or file) to a hashing algorithm, which processes the data and generates a unique hash value. The resulting hash value is always the same length, regardless of the size of the input data.
Here are some common hashing algorithms:
Python Hashing Calculator
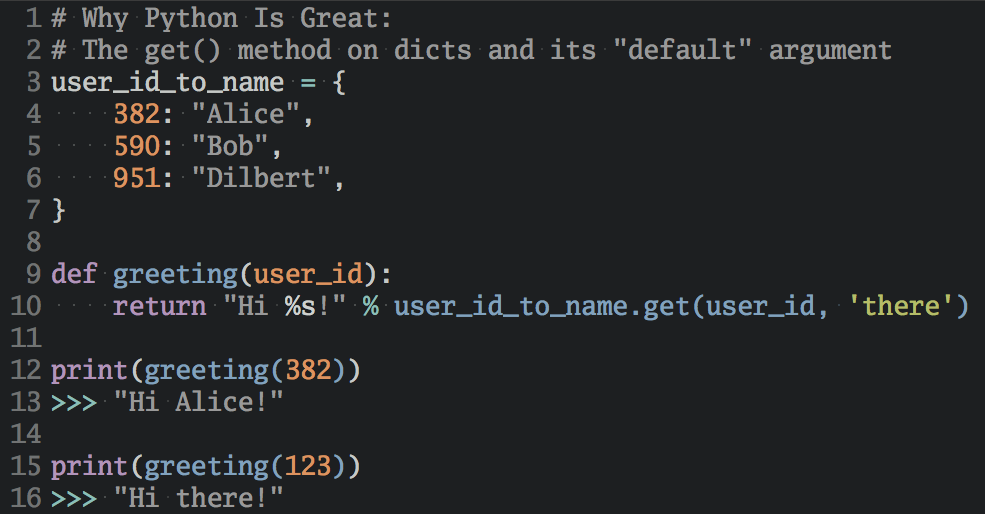
You can use the following Python code to calculate hash values:
import hashlib
def calculate_hash(input_string):
Create a new MD5 or SHA-256 hashing object
if 'md5' in input_string.lower():
hashing_object = hashlib.md5()
elif 'sha-256' in input_string.lower():
hashing_object = hashlib.sha256()
else:
print("Invalid algorithm. Defaulting to SHA-256.")
hashing_object = hashlib.sha256()
Feed the input string to the hashing object
hashing_object.update(input_string.encode('utf-8'))
Get the hashed value
hash_value = hashing_object.hexdigest()
return hash_value
Test the hashing calculator
input_string = "Hello, World!"
print(calculate_hash(input_string))
How to Use the Python Hashing Calculator
To use this calculator, simply replace input_string with your desired input data. The code will calculate and display the hashed value.
Here's a step-by-step guide:
Copy the Python code above. Replaceinput_string with your desired input data (text or file path). Run the code using a Python IDE like PyCharm, Visual Studio Code, or Spyder. The code will calculate and display the hashed value.
Limitations of Hashing
Hashing has some limitations:
Reversibility: It is difficult to reverse-engineer the original input data from the hash value (unless you have access to the same hashing algorithm used). Collision Resistance: It is theoretically possible for two different input strings to produce the same hash value, known as a collision. Hash Value Length: The length of the hash value depends on the chosen hashing algorithm.In conclusion, Python provides an easy way to calculate hash values using various algorithms like MD5 and SHA-256. This calculator can be used for data integrity checks, password storage, and digital signatures. Remember that hashing has some limitations, so it's essential to choose the right hashing algorithm and consider the trade-offs when implementing your solution.
Python hashing example

Here's a Python example for demonstrating basic cryptographic concepts with hash functions:
import hashlib
import binascii
Using hashlib library for SHA-256 and MD5 hashing
def generate_hash(input_string):
SHA-256 Hashing
sha256_hash = hashlib.sha256(input_string.encode())

print("SHA-256 Hash:", sha256_hash.hexdigest())
MD5 Hashing
md5_hash = hashlib.md5(input_string.encode())
print("MD5 Hash:", md5_hash.hexdigest())
Example usage
input_text = "Hello, World!"
generate_hash(input_text)
Example usage for binary data (e.g., image files)
binary_data = b'x00x01x02x03'
sha256_hash = hashlib.sha256(binary_data)
print("SHA-256 Hash of Binary Data:", sha256_hash.hexdigest())
To better understand the concept, let's break down what happens in this example:
1. Input String: You provide an input string that you want to hash (e.g., "Hello, World!"). This could be any type of text data or binary information.
2. SHA-256 Hashing: The hashlib library is used to generate the SHA-256 cryptographic hash for your input string. SHA-256 is a widely used digital signature algorithm that provides a 256-bit (64-character hexadecimal) output, which is difficult to reverse-engineer and ensures data integrity.
3. MD5 Hashing: Additionally, MD5 (Message-Digest Algorithm 5) hashing is performed on the same input string using hashlib. MD5 generates a 128-bit (32-character hexadecimal) output hash. While MD5 is considered weaker than SHA-256, it's still suitable for certain applications.
4. Binary Data Hashing: In the second part of the example, you provide binary data (e.g., an image file). This could be any type of binary information that you want to hash. The hashlib library again generates a SHA-256 hash for this binary data.
Key Takeaways:
1. Cryptographic Hashing: In cryptography, hashing is used to create a digital fingerprint of your data. Hash functions take an input (like text or binary data) and generate an output hash that can be compared for equality or authenticity.
2. Collision-Resistant: The outputs of these cryptographic hash functions are collision-resistant, meaning it's computationally infeasible to find two different inputs with the same output hash.
3. Data Integrity: Hashes ensure the integrity of your data by providing a unique fingerprint. Even if you modify or corrupt the original input, the generated hash will be different from the expected result.
4. Reversibility: The hashing process is designed to be non-reversible. It's extremely difficult (or impossible) for an attacker to take a given hash output and recover the original input data.
These concepts are essential in various applications such as digital signatures, data verification, and authentication.