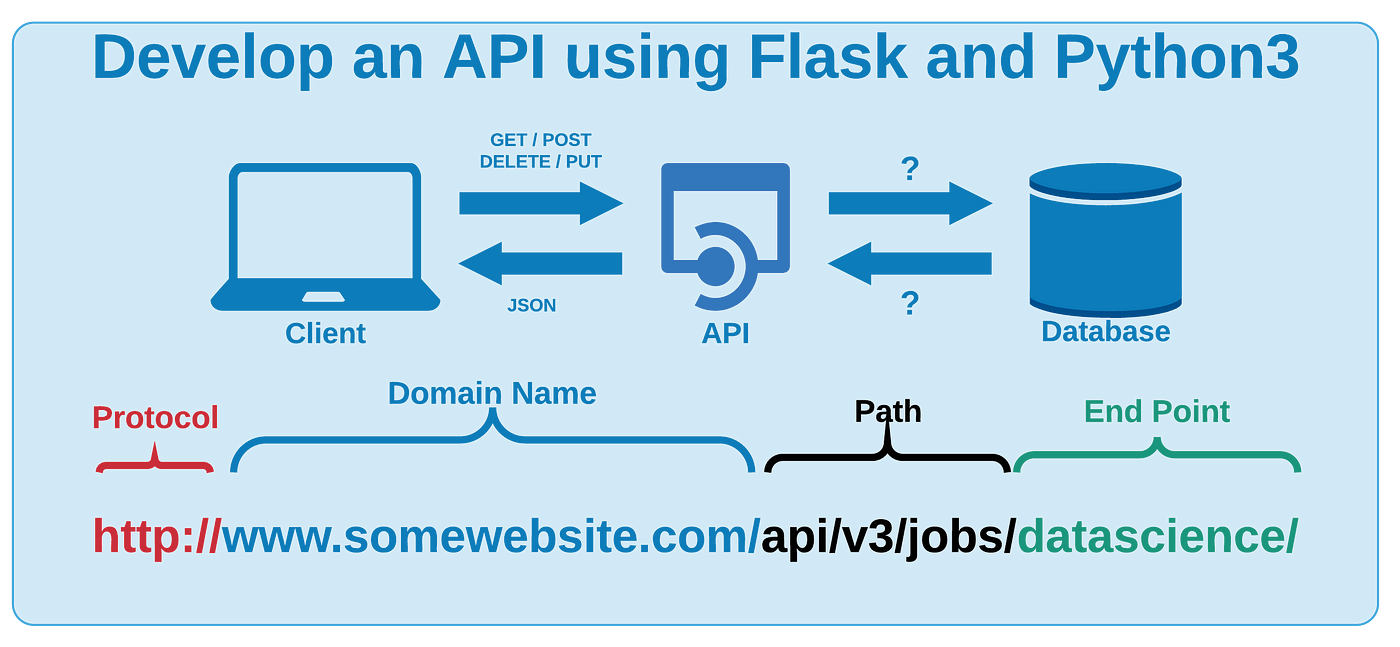
Python owasp vulnerabilities
Python owasp vulnerabilities
I'm happy to respond in English for you!
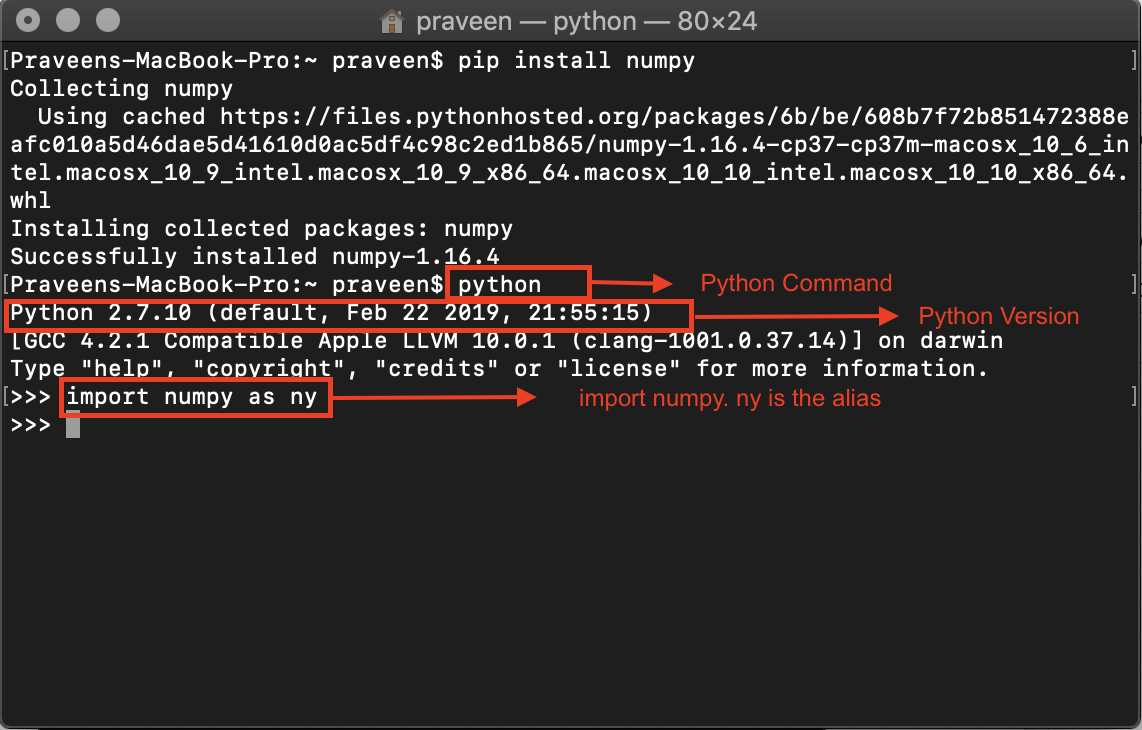
Python is a popular programming language used by many developers and security researchers alike. As such, it's not immune to common web application security vulnerabilities, as identified by OWASP (Open Web Application Security Project). Here are some Python-specific vulnerabilities and best practices:
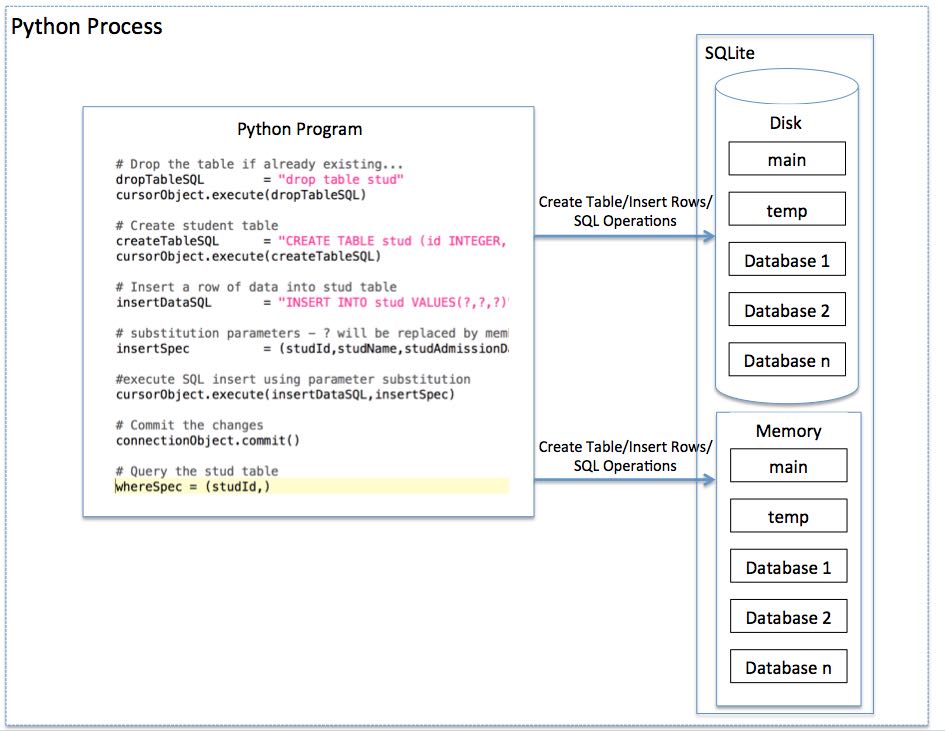
SQL Injection: This vulnerability occurs when an attacker injects malicious SQL code into a database query. To prevent this, always use parameterized queries or ORMs (Object-Relational Mappers) that properly escape user input.Best practice: Use sqlalchemy or peewee to create robust and secure database interactions.

subprocess with proper escaping of user input.
Best practice: Avoid using os.system() or commands.getoutput(). Instead, use subprocess.run() with the check=True argument to ensure command execution is monitored and controlled.

bleach or html5lib.
Best practice: Use a robust HTML sanitizer to ensure user input is properly cleaned before being rendered in the browser.
Insecure Direct Object Reference (IDOR): This occurs when an attacker exploits direct access to sensitive data without proper authorization. To prevent this, use object-oriented programming and encapsulation to limit access to sensitive data.Best practice: Use Python's property decorator to control access to sensitive attributes and methods.
bcrypt and implement robust authentication mechanisms.
Best practice: Implement a strong authentication framework using libraries like flask-security or django-auth.
os.path.join() to ensure proper file path construction.
Best practice: Avoid using os.system() with user-input file paths. Instead, use subprocess.run() with the cwd argument to control the working directory and prevent FIV.
logging.
Best practice: Use Python's try/finally block to ensure proper resource cleanup even in the presence of exceptions.
urlparse.
Best practice: Use a robust URL parser to ensure user input is properly cleaned before being used for redirection.
Unvalidated User-Input: This occurs when an attacker injects malicious user-input data into a Python script or web application. To prevent this, validate and sanitize user input using libraries likew3lib.
Best practice: Use Python's built-in str.isdigit() and re modules to ensure user input is properly validated and sanitized.
Best practice: Implement a Content Security Policy (CSP) and other security headers using libraries like flask-security or django-csp.
Remember, secure coding practices are essential for protecting your users' data. Always stay up-to-date with the latest OWASP guidelines and best practices to ensure your Python applications remain secure and robust!
What is the purpose of the Python OWASP project?
The Python OWASP (Open Web Application Security Project) project has a noble purpose - to improve the security posture of web applications written in Python. The project's primary objective is to provide a comprehensive and reliable set of best practices, tools, and documentation for building secure Python-based web applications.
OWASP is an international non-profit organization that aims to make the web safer by providing practical resources and knowledge about application security. By focusing specifically on Python, the OWASP project addresses a critical need in the developer community - creating a trusted ecosystem for building robust and secure web applications.
The Python OWASP project's main goals are:
Some specific outputs from the project include:
Python Security Cheat Sheet: A concise reference guide providing best practices for securing Python-based web applications.
By supporting the Python OWASP project, developers can ensure that their applications are built using secure principles, reducing the risk of exploitation by attackers and protecting users' sensitive data.