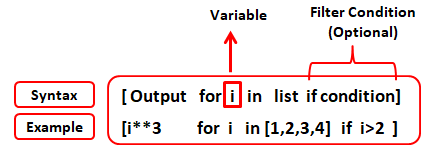
Python api authentication json
Python api authentication json
Here's a detailed explanation of JSON-based API authentication using Python:
API (Application Programming Interface) is an interface that allows different applications to communicate with each other. One of the most common methods for securing APIs is through JSON-based authentication, which utilizes JSON (JavaScript Object Notation) data interchange format.
JSON is a lightweight data-interchange format that is easy to read and write. It is widely used in web development as a means of exchanging data between server and client. In this context, it's used to authenticate users and validate their requests.
API authentication using JSON typically involves the following steps:
Token Generation: The API generates a unique token for each user after verifying their credentials (username and password). This token is used for all subsequent API requests made by that user. JSON Web Token (JWT): A JSON Web Token (JWT) is generated using the username, timestamp, and a secret key. JWTs are digitally signed tokens that contain payload information. Token Verification: Upon receiving an API request, the server verifies the token's authenticity using the provided username and password or other validation mechanisms. Authentication: If the token is valid, the server authenticates the user and grants access to the requested resources.Python provides a range of libraries for JSON-based authentication. For example:
flask-jwt-extended: This library extends the popular Flask-JWT library by adding additional features such as JSON Web Token (JWT) validation, token refresh, and more. pyjwt: PyJWT is a Python package for generating and verifying JWTs. It provides support for various algorithms and signatures.Here's an example of using flask-jwt-extended for JSON-based authentication in Python:
app.py
from flask import Flask, request, jsonifyfrom flask_jwt_extended import JWTManager, jwt_required, create_access_token
app = Flask(name)
app.config["SECRET_KEY"] = "super-secret-key"
jwt = JWTManager(app)
@app.route("/login", methods=["POST"])
def login():
username = request.json.get("username")
password = request.json.get("password")
Verify credentialsif verify_credentials(username, password):
access_token = create_access_token(identity=username)
return jsonify(access_token=access_token), 200
@app.route("/protected", methods=["GET"])
@jwt_required
def protected():
return jsonify(message="This view is protected"), 200
if name == "main":
app.run(debug=True)
In this example, we define two routes: /login and /protected. The /login route accepts a JSON payload with username and password. It verifies the credentials using the verify_credentials function (not shown in this example) and generates an access token if the credentials are valid.
The /protected route is only accessible to users who have provided a valid access token in their request headers.
Verification
To verify the authenticity of incoming requests, we use the @jwt_required decorator on the /protected route. This decorator checks for the presence of an access token in the request headers and verifies its validity using the jwt.verify_token() function (not shown in this example).
This is just a basic example of JSON-based authentication using Python. You can customize and extend it to suit your specific use case.
Conclusion
In conclusion, JSON-based API authentication provides a robust way to secure APIs by utilizing digitally signed tokens that contain payload information. Python libraries such as flask-jwt-extended and pyjwt provide support for generating and verifying JWTs, making it easy to implement this type of authentication in your projects.
How to secure APIs in Python?
Securing APIs in Python! A crucial aspect of building robust and trustworthy applications. Here's a comprehensive guide on how to do just that.
Authentication
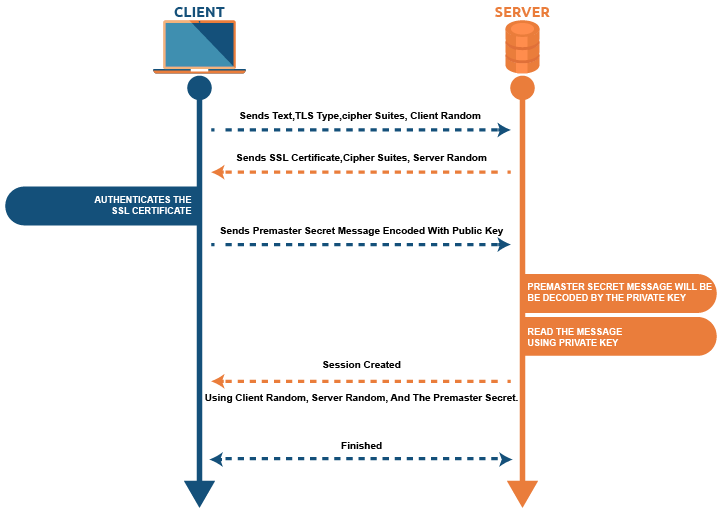
APIs need authentication to verify the identity of users or clients making requests. In Python, you can use libraries like Flask-JWT-Extended (for JSON Web Tokens) or PyJWT (for JSON Web Tokens) for JWT-based authentication.
Here's a simple example with Flask-JWT-Extended:
from flask import Flask, request
from flask_jwt_extended import JWTManager, jwt_required
app = Flask(name)
app.config["SECRET_KEY"] = "your_secret_key_here"
jwt = JWTManager(app)
@app.route("/login", methods=["POST"])
def login():
username = request.json.get("username")
password = request.json.get("password")
Your login logic here...
return {"auth_token": generate_jwt_token(username)}
@app.route("/protected", methods=["GET"], endpoint="protected")
@jwt_required
def protected():
return "Hello, authenticated user!"
if name == "main":
app.run(debug=True)
Authorization
Once you have authentication in place, it's time to think about authorization. You can implement role-based access control (RBAC) or attribute-based access control (ABAC). For RBAC, libraries like Flask-RBAC and PyRbac are available.
Here's a basic example with Flask-RBAC:
from flask import Flask
from flask_rbac import RoleDefinitionStore
app = Flask(name)
rds = RoleDefinitionStore(app)
Define roles and permissions...
@app.route("/admin", methods=["GET"], endpoint="admin")
@has_role("admin")
def admin():
return "Hello, admin!"
if name == "main":
app.run(debug=True)
Data Encryption
To protect data in transit, you can use libraries like PyNaCl (for NaCl encryption) or cryptography (for various encryption algorithms).
Here's a simple example with PyNaCl:
import nacl.secret
key = nacl.random secretpublicKey=nacl.generate_secret_key()
encrypted_data = key.encrypt("your_encrypted_data_here")
Input Validation
Validate all user inputs to prevent SQL injection, cross-site scripting (XSS), and other attacks. Use libraries like Werkzeug (for validation) or flask-wtf (for form validation).
Here's a basic example with Werkzeug:
from werkzeug.security import validate_password
def login():
username = request.form.get("username")
password = request.form.get("password")
Validate input...
if not validate_username(username):
return "Invalid username...", 400
elif not validate_password(password):
return "Invalid password...", 400
Login logic here...
return {"auth_token": generate_jwt_token(username)}
Error Handling
Handle errors gracefully by logging them and displaying user-friendly error messages. Use libraries like Flask-Logconfig (for logging) or Flask-WTF (for error handling).
Here's a basic example with Flask-Logconfig:
import logging
app.config["LOGGING_LEVEL"] = "DEBUG"
logging.basicConfig(level=app.config["LOGGING_LEVEL"])
@app.errorhandler(404)
def not_found(error):
return "Page not found...", 404
if name == "main":
app.run(debug=True)
Code Reviews and Audits
Regularly review your code for security vulnerabilities and perform audits to identify potential issues.
Here are some final tips:
Always follow best practices for secure coding. Use reputable libraries and dependencies. Keep your Python versions up-to-date, as newer versions often include security patches. Implement a bug bounty program or participate in open-source projects to stay informed about the latest security threats.By following these guidelines and implementing proper authentication, authorization, data encryption, input validation, error handling, and code reviews/audits, you'll significantly reduce the risk of security breaches in your Python APIs.