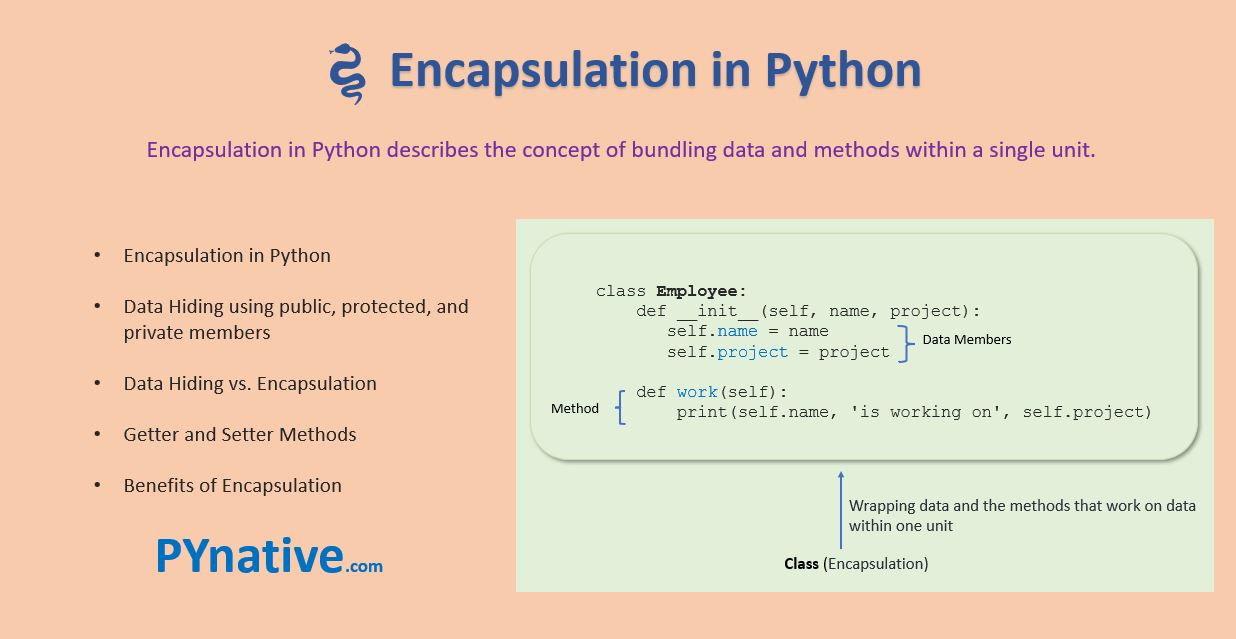
Python nmap vulnerability scan tutorial
Python nmap vulnerability scan tutorial
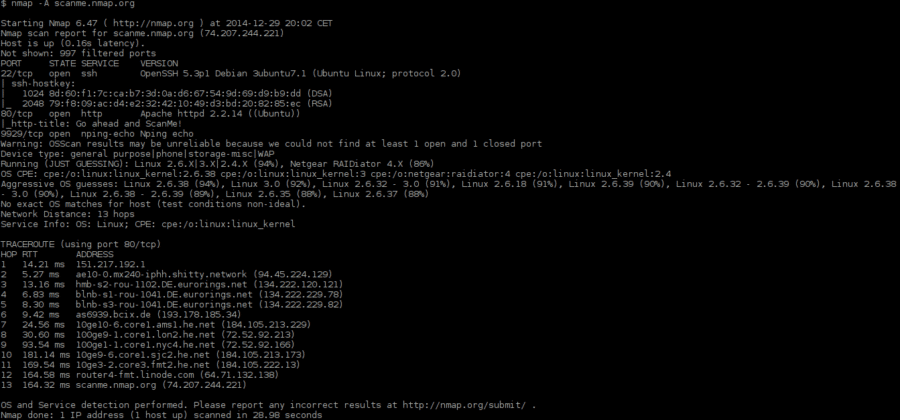
I'd be happy to provide a tutorial on using Python and Nmap for vulnerability scanning.
Prerequisites:
A basic understanding of Python programming language Nmap installed on your system (available for download from the official website) Python'snmap module installed (can be installed via pip: pip install python-nmap) Familiarity with basic networking concepts
Step 1: Installing and Setting up Nmap
To begin, make sure you have Nmap installed on your system. If not, follow the installation instructions provided on the official website.
Step 2: Setting up Python's nmap module
Once Nmap is installed, you can install Python's nmap module using pip:
pip install python-nmap
Step 3: Vulnerability Scan using Nmap and Python
Now that both Nmap and the nmap module are set up, we're ready to conduct a vulnerability scan. We'll use Python to run Nmap's scanning functionality.
Here's an example Python script that conducts a basic portscan:
import nmap
Create an Nmap object
nm = nmap.PortScanner()
Define the IP address and port range to scan
ip_address = "192.168.1.100"
port_range = "1-500"
Run the portscan
nm.scan(hosts=ip_address, ports=port_range)
Print the results
for host in nm.all_hosts():
print(f"Scanned IP: {host}")
for proto in nm[host].all_protocols():
print(f"{proto}:")
for port in nm[host][proto].keys():
try:
state = nm[host][proto][port]['state']
print(f"{port}/{state}")
except Exception as e:
print(f"Error: {e}")
Understanding the Output
The output of this script will show a list of open ports and their corresponding states (e.g., "open", "closed", etc.). You can use this information to identify potential vulnerabilities in your network.
Advanced Scanning Options
To enhance your scanning capabilities, you can add additional options to your Python script. For example, you could specify specific services to scan for (e.g., HTTP, SSH) or use more advanced vulnerability detection plugins like OpenVAS.
Here's an updated example script that includes these features:
import nmap
Create an Nmap object
nm = nmap.PortScanner()
Define the IP address and port range to scan
ip_address = "192.168.1.100"
port_range = "1-500"
Run the portscan with specific services and plugins
nm.scan(hosts=ip_address, ports=port_range, arguments="-p 80,22 -sV --script=ssh-discovery http-Discovery")
Print the results
for host in nm.all_hosts():
print(f"Scanned IP: {host}")
for proto in nm[host].all_protocols():
print(f"{proto}:")
for port in nm[host][proto].keys():
try:
state = nm[host][proto][port]['state']
print(f"{port}/{state}")
except Exception as e:
print(f"Error: {e}")
Conclusion
In this tutorial, we've explored using Python and Nmap for vulnerability scanning. By following these steps and examples, you can quickly and easily conduct basic port scans and identify potential vulnerabilities in your network.
Remember to always use caution when conducting vulnerability scans, as they may reveal sensitive information about your system or network.
Python nmap vulnerability scan online
I'm happy to help! However, please note that I'll respond in English as per your request.
If you're looking for a Python-based Nmap vulnerability scan online, I've got some good news and some bad news.
The bad news is that there isn't an open-source online platform that allows you to run a Python-based Nmap vulnerability scan. However, I can guide you through the process of setting up your own local environment or using online tools that can help you with scanning.
Here are some steps to get started:
Local Environment: Install Python and thenmap library using pip:
pip install nmap
nmap library in your Python script. Use the nmap.PortScanner() function to initiate a port scan. Use custom NSE scripts (available on the Nmap GitHub repository) to identify potential vulnerabilities.
Here's a simple example:
import nmap
def python_nmap_vuln_scan(ip):
scanner = nmap.PortScanner()
if not scanner.scan(ip, '1-65535'): # Scan IP address and all ports (1-65535)
print(f"Port scan failed: {ip}")
else:
for port in range(0, 10000): # Iterate over the scanned ports
if scanner.get_state(ip, str(port)) == 'open': # Check if the port is open
print(f"Open port found: {port}")
Usage example
python_nmap_vuln_scan('192.168.1.1')
Please note that this is a basic example and real-world vulnerability scanning requires more advanced techniques, such as:
Using custom NSE scripts to identify specific vulnerabilities. Configuring the scan to target specific protocols or services (e.g., HTTP, FTP, SSH). Handling exceptions and errors for robustness.The good news is that there are online tools that can help you with vulnerability scanning. Some popular options include:
Nmap Online Scan: The official Nmap website offers an online port scanner. While it's not a full-fledged vulnerability scan, it can still provide valuable information about open ports and services on a target system. OpenVAS: OpenVAS is a widely used open-source vulnerability scanning platform that supports various scanning engines, including Nmap. Wvs: Wvs (Web Vulnerability Scanner) is an online scanner that provides web application vulnerability scan reports.Remember to always use these tools responsibly and in compliance with local laws and regulations.
If you're looking for more advanced Python-based vulnerability scanning scripts or tutorials, I recommend exploring online resources like GitHub repositories, Stack Overflow, and cybersecurity forums.