Python nmap vulnerability scan tutorial
Python nmap vulnerability scan tutorial
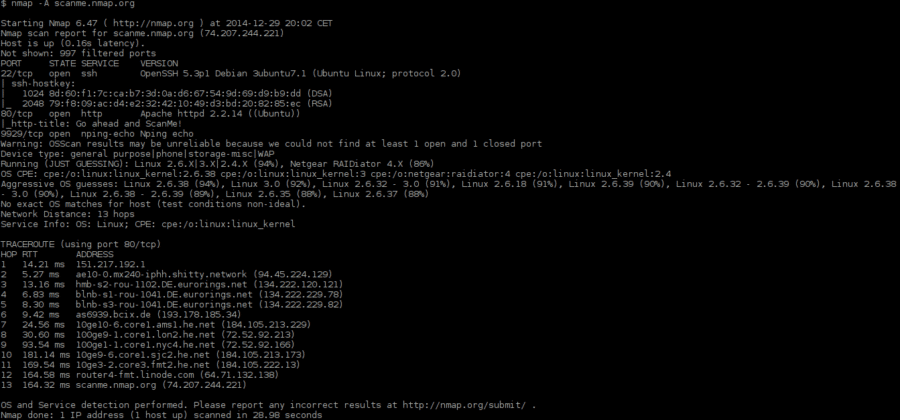
I'd be happy to provide a tutorial on using Python and Nmap for vulnerability scanning.
Prerequisites:
A basic understanding of Python programming language Nmap installed on your system (available for download from the official website) Python'snmap module installed (can be installed via pip: pip install python-nmap) Familiarity with basic networking concepts
Step 1: Installing and Setting up Nmap
To begin, make sure you have Nmap installed on your system. If not, follow the installation instructions provided on the official website.
Step 2: Setting up Python's nmap module
Once Nmap is installed, you can install Python's nmap module using pip:
pip install python-nmap
Step 3: Vulnerability Scan using Nmap and Python
Now that both Nmap and the nmap module are set up, we're ready to conduct a vulnerability scan. We'll use Python to run Nmap's scanning functionality.
Here's an example Python script that conducts a basic portscan:
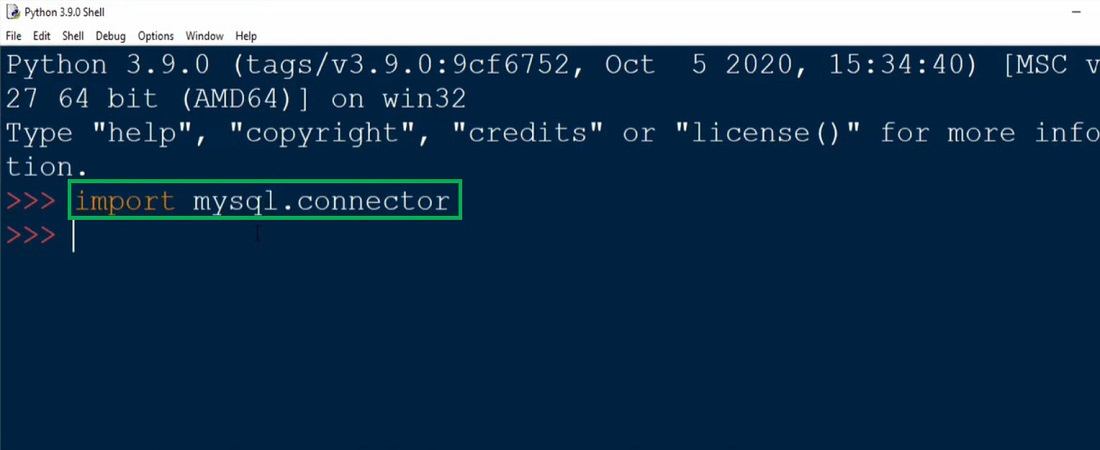
import nmap
Create an Nmap object
nm = nmap.PortScanner()
Define the IP address and port range to scan
ip_address = "192.168.1.100"
port_range = "1-500"
Run the portscan
nm.scan(hosts=ip_address, ports=port_range)
Print the results
for host in nm.all_hosts():
print(f"Scanned IP: {host}")
for proto in nm[host].all_protocols():
print(f"{proto}:")
for port in nm[host][proto].keys():
try:
state = nm[host][proto][port]['state']
print(f"{port}/{state}")
except Exception as e:
print(f"Error: {e}")
Understanding the Output
The output of this script will show a list of open ports and their corresponding states (e.g., "open", "closed", etc.). You can use this information to identify potential vulnerabilities in your network.
Advanced Scanning Options
To enhance your scanning capabilities, you can add additional options to your Python script. For example, you could specify specific services to scan for (e.g., HTTP, SSH) or use more advanced vulnerability detection plugins like OpenVAS.
Here's an updated example script that includes these features:
import nmap
Create an Nmap object
nm = nmap.PortScanner()
Define the IP address and port range to scan
ip_address = "192.168.1.100"
port_range = "1-500"
Run the portscan with specific services and plugins
nm.scan(hosts=ip_address, ports=port_range, arguments="-p 80,22 -sV --script=ssh-discovery http-Discovery")
Print the results
for host in nm.all_hosts():
print(f"Scanned IP: {host}")
for proto in nm[host].all_protocols():
print(f"{proto}:")
for port in nm[host][proto].keys():
try:
state = nm[host][proto][port]['state']
print(f"{port}/{state}")
except Exception as e:
print(f"Error: {e}")
Conclusion
In this tutorial, we've explored using Python and Nmap for vulnerability scanning. By following these steps and examples, you can quickly and easily conduct basic port scans and identify potential vulnerabilities in your network.
Remember to always use caution when conducting vulnerability scans, as they may reveal sensitive information about your system or network.
Python nmap vulnerability scan github
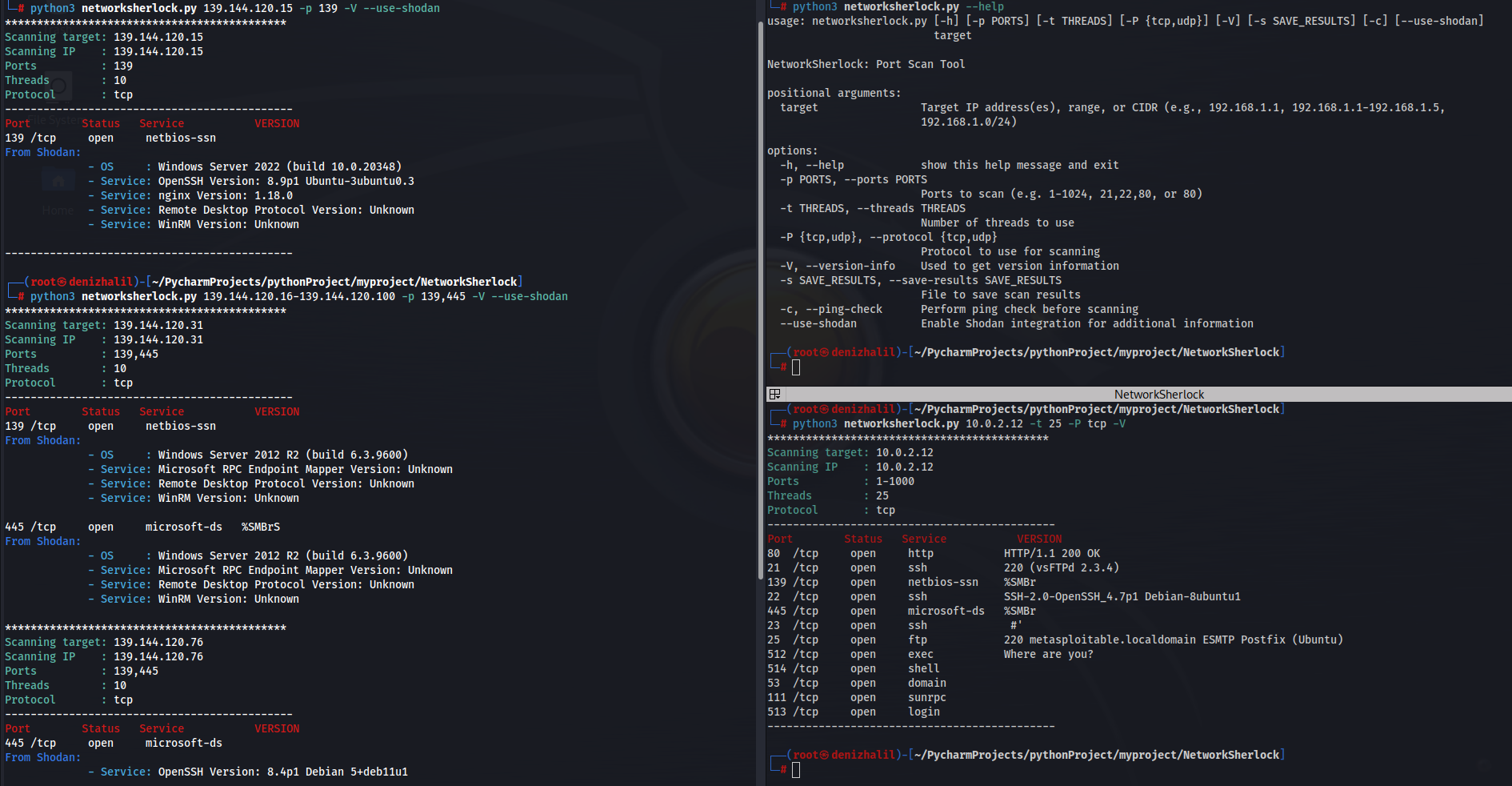
I'll respond in English only this time!
Here are some details about a Python Nmap vulnerability scan using GitHub:
Nmap: Network Mapper (Nmap) is a free and open-source network scanning tool used for network discovery, security auditing, and asset management.
Python Nmap Library: The Python Nmap library provides an easy-to-use interface to interact with Nmap from your Python scripts. It allows you to execute various Nmap commands, retrieve the results, and analyze them further in your Python code.
GitHub Repository: The GitHub repository for the Python Nmap library is located at: https://github.com/nmap-python/python-nmap
Here's an example of how you can use the Python Nmap library to scan a network for vulnerabilities:
from nmap import PortScanner, PortScannerError
import json
def main():
scanner = PortScanner()
try:
Scan the network
host = "192.168.1.100" # Replace with the IP address you want to scan
os = "linux" # Operating System of the host
scanner.scan(hosts=host, ports="1-1024", options="-v -A --os=%s" % (os))
Print the results
for host in sorted(scanner.all_hosts()):
print("Scan report for host: ", host)
for proto Protocol in sorted(scannerprotocols()):
print(f"{proto}:")
try:
for port in sorted(scanner[host][proto].keys()):
state = scanner[host][proto].get(port)['state']
if state == "open":
print("Port {}: Open".format(int(port)))
else:
print("Port {}: Closed".format(int(port)))
except:
print(f"{host}:{proto} not scanned due to some reasons")
except PortScannerError as e:
print("An error occurred: ", str(e))
if name == "main":
main()
GitHub Issues and Pull Requests: The GitHub repository for the Python Nmap library is actively maintained, with many open issues and pull requests. You can participate in discussions, report bugs, or contribute new features to the project.
Example Vulnerability Scan Command: Using the nmap command-line tool, you can run a vulnerability scan like this:
sudo nmap -A -v -sV --script "default, http-methods, vuln"
This will perform a comprehensive scan of the network, including open ports, operating system detection, and various vulnerability checks.
Please note that this is just an example code snippet. You should always consult the official documentation and usage guidelines for both Nmap and the Python Nmap library before conducting actual scans.